'Not one and done': How Singapore's police and government tech agency combat ever-evolving scams
One of the government's latest anti-scam products involves a phishing detection platform to disrupt fraud websites.
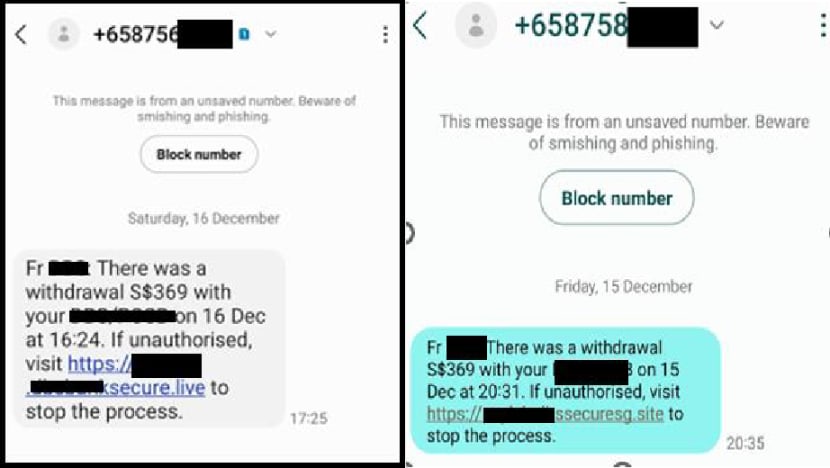
Screenshots of fake SMSes purportedly from banks sent to victims. (Images: Singapore Police Force)

This audio is generated by an AI tool.
SINGAPORE: Scams are on the rise but the fundamentals remain the same for fraudsters trying to cheat people of their hard-earned savings: They cast out as wide a net as possible to reel in unsuspecting victims.
And for those in the everyday business of fighting the scam scourge, they have their work cut out combatting operations that are growing more sophisticated by the minute.
The Singapore Police Force (SPF) said the scam cases increased by 46.8 per cent from 31,728 in 2022 to 46,563 in 2023 - the biggest number since it began tracking scams in 2016.
And over a year into its inception, the Anti-Scam Command (ASComm) has already seen scam variants evolve and even draw on artificial intelligence.
But the authorities are optimistic about keeping on top of it all, as the head of the anti-scam "nerve centre", Senior Assistant Commissioner of Police Shee Tek Tze, told CNA.
"We will monitor the trends, we will see which trend is spiking faster than others and then we will devote resources and come up with ways to tackle those, on a daily and weekly basis," said SAC Shee.
That was how the police caught on to malware scams when they first emerged sometime in 2022. This variant involves fraudsters infecting Android phones with malware, accessing the phones and consequently siphoning money via mobile banking apps.
At least S$34.1 million was lost to malware scammers in 2023.
"We started noticing that there are a lot of reports where the victim said that, 'Actually I didn't do any transfer, but I don't know why, I discovered that money is gone from my account'," said SAC Shee.
"We did our investigation, part of which was that we conducted some forensic examination of the victim's phone and in some of the phones we found the malware, and that is what alerted us to the start of scammers using this as a tool."

But scammers have managed to react just as fast, with some even wiping out phones to frustrate forensic efforts.
The Government Technology Agency (GovTech)'s principal product manager in anti-scam products, Mark Chen, described the fight against scams as an "ongoing" battle.
“It's not one and done, you can't develop a tool and let it run in the background. The scammers are going to react very quickly, they will have evasion techniques," said Mr Chen.
His team builds technological solutions to disrupt scammers, as part of efforts by GovTech to support law enforcement.
Mr Chen pointed to just how speedily a scammer could hijack a phone, as an example of how they "really are levelling up a lot."
After a user installs a malicious, malware-infected app on the phone, the user would need to enable accessibility permissions, allowing the app to access the phone remotely.
The initial reason for such a function was for people with disabilities, who needed to have an app read to them, for example.
Once enabled, the swindler will take over the phone to grant other permissions, which flash across the screen in a series of lightning-fast pop-ups.
“You can't even see what you allowed them to do,” Mr Chen said, pointing out how scammers then use the permissions to grant them everything else they need - the ability to read SMSes, intercept calls and even obtain locations.
“It’s all instant because it's remote already. Now they can tap on your phone as if they are you - because you gave them that permission."
FROM WEBSITES TO SMSES TO CHAT APPS
Though its efforts are often unseen, GovTech’s anti-scam products team has nevertheless been gaining momentum in taking down hoax websites masquerading as official ones.
In December 2022, GovTech and the Ministry of Home Affairs (MHA) rolled out a detection tool called PhishMonSG, which proactively identifies impostor websites so that they can be taken down.
The team's latest product, the Scam Analytics and Tactical Intervention System (SATIS), is jointly developed by GovTech and the Home Team’s science and technology agency HTX.
A step up from PhishMonSG, SATIS both hunts and disrupts scam sites and has expanded beyond government websites to include bank phishing sites, sites hosting malware and those used in impersonation scams.
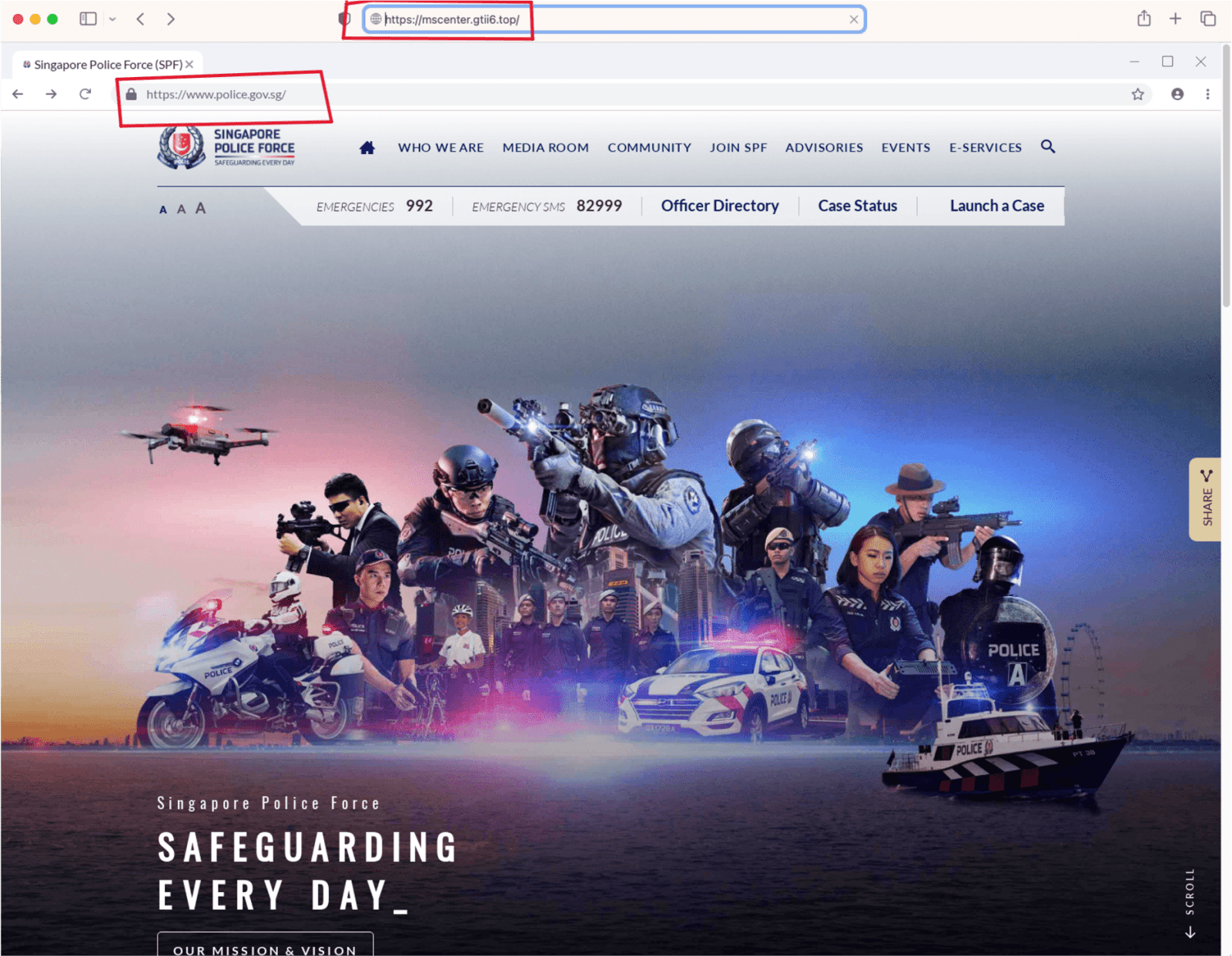

SATIS does the work in three stages: First, consolidating information about threats, partly through using artificial intelligence to crawl the World Wide Web for potential scams; next, analysing the information to determine if the sites are malicious; and finally taking down or blocking verified scams.
In the last stage, GovTech works with Google to use the tech giant's Web Risk feature, which can block reported malicious websites on supported browsers including Chrome, Firefox and Safari. A person visiting a blocked site will see a warning instead.
To date, GovTech has disrupted over 16,000 potentially harmful sites, ranging from job scam ones to fraudulent e-commerce pages.
Even then, fraudsters have shifted to different platforms to continue their dirty work.
They have spoofed official sender IDs to send SMSes containing links to fraudulent websites, to phish for information. And when Singapore responded by introducing a SMS Sender ID Registry, scammers pivoted again.
"We are seeing now ... more than 50 per cent are on either chat apps like WhatsApp, like Telegram ... or they use social media platforms like Facebook or Instagram,” said SAC Chee, the head of the Anti-Scam Command.
Assistant director of GovTech's cyber security group and anti-scam products Andre Ng added that the lessons learnt from protecting government websites have been applied towards developing more scam countermeasures.
"There are hundreds, if not thousands, of scams that are directed at Singaporeans on a daily basis," he said. "So we are trying to solve the problem of how do we scale up police operations or law enforcement operations at a pace where they can keep up with the kind of load."
WHAT YOU NEED TO KNOW
No matter the platform or conduit, the same principles remain, said SAC Chee.
"At a very fundamental level, scams are about the scammer designing some sort of deceit, being able to deliver that deceit, convince potential victims of that deceit ... and the outcome they want to achieve is to be able to get money from the victims."
This can then be distilled into two broad goals achieving that same outcome: To obtain the banking credentials of victims and make transactions; or have the victims believe the deceit and make the transfer themselves.
The good news is that even without the tech know-how, users can still take precautions against scams.
GovTech’s Mr Ng boiled down his advice to simply taking a step back when dealing with a request involving sensitive information.
“Think about why they might be asking you and verify as much as possible. So the ploys can change, their excuse can change. It could be a fake friend call, one day it could take place over a website.”
“Just having that pause and thinking for just five seconds whether am I doing the right thing or not, or (if) the urgency (is) even legitimate. Questioning that helps a lot in preventing a lot of these kind of cases,” he said.
Part of SPF’s strategy is to beef up the public's knowledge and also reach out to as many potential victims as possible, especially on platforms used by scammers.
When law enforcement agencies observe a spike in a scam variant, they establish the “kill-chain” - or phases of an attack from an attacker's perspective - before sieving out and publishing relevant information through advisories, news releases and social media posts.
This hopefully helps the public “raise a red flag in their minds", should they come across similar circumstances, said SAC Shee.
“An easy way to deal with this is for police to put out a website and then just put everything there and say that I have done my due diligence ... If you, as a member of public, don’t read it, it’s your problem," he added.
"But we don't see it as that. We do what we think is effective.”